Advanced Cybersecurity Audit & Targeted Penetration Testing for Complex Systems

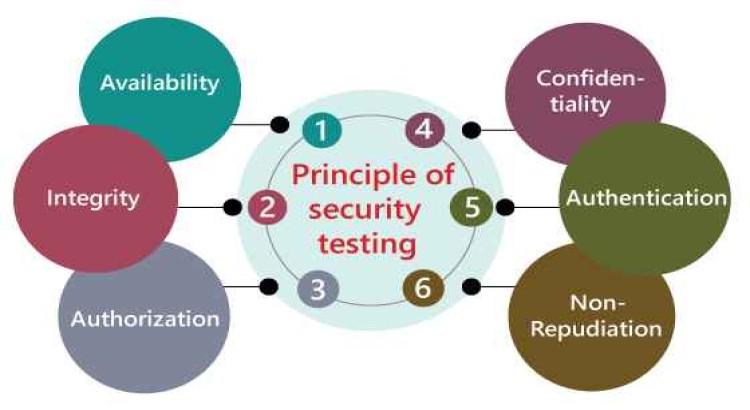
About this Service
In a world of increasingly sophisticated cyber threats, generic vulnerability scans are no longer sufficient.
This service provides a targeted, standards-based penetration testing and cybersecurity audit specifically designed for production-grade systems and enterprise-level applications.
Using a combination of manual exploitation techniques, custom tooling, and methodical auditing frameworks, I help you identify and remediate real security weaknesses — before attackers do.
Scope of Work
1. Penetration Testing (PT) & Exploitation
- Threat modeling based on your architecture (STRIDE / DREAD model)
- Black-box and grey-box testing approaches
- Manual identification and exploitation of:
- Input injection flaws (SQLi, XSS, SSTI, RCE)
- Insecure session/token handling
- Broken authentication and access control issues (IDOR, privilege escalation)
- CSRF, SSRF, open redirects, and insecure deserialization
- Lateral movement simulation (internal network only, if access is provided)
2. Infrastructure & Cloud Exposure Testing
- Scanning and validation of exposed services (Nmap, Shodan-like fingerprinting)
- Assessment of firewall policies and ingress rules
- Misconfigured cloud services (e.g., open S3 buckets, overly permissive IAM roles)
- Subdomain enumeration and takeover checks
3. Application & API Testing
- Deep testing of RESTful and GraphQL APIs
- Header security, rate-limiting, token leakage
- Broken object/property-level authorization
- OAuth/OpenID misconfigurations
4. Compliance-Centric Audit
- Mapping findings to:
- OWASP Top 10
- SANS Top 25
- MITRE ATT&CK framework (when applicable)
- Regulatory standards (ISO 27001, GDPR, HIPAA, PCI-DSS)
Deliverables
You will receive a detailed technical report covering:
- Executive Summary (risk heatmap + priority matrix)
- Threat modeling diagram (if applicable)
- Vulnerabilities categorized by CVSSv3.1 score
- Exploitable PoCs + reproduction steps
- Clear and actionable remediation instructions
- Mitigation strategy prioritization (Quick wins vs. Long-term hardening)
Post-Audit Support
- 1x consultation session with your technical team
- 10-day post-delivery window for clarifications or technical Q&A
- Optional retesting after remediation (can be quoted separately)
Toolset
- Burp Suite Pro, OWASP ZAP, Nmap, SQLMap, Gobuster, ffuf, Nikto, Amass, JWT Cracker, custom Python/Go scripts, and more
- Manual testing is always prioritized over automated scanning
Ideal for
- Fintech / SaaS platforms
- E-commerce portals with payment flows
- API-first backends or mobile-integrated systems
- Applications handling sensitive or regulated data
Service Features
- ● Remote session-based testing with secure access protocols
- ● Full compliance-ready technical documentation
- ● Risk-based prioritization of findings
- ● Post-audit consultation & support
About the Seller
From
United States
Member Since
Oct 2024
Skills:
Basic






Join as a freelancer or client
Join as a Freelancer
Join as a Client