Fortify Your Defenses: Advanced Firewall & IDS/IPS Implementation

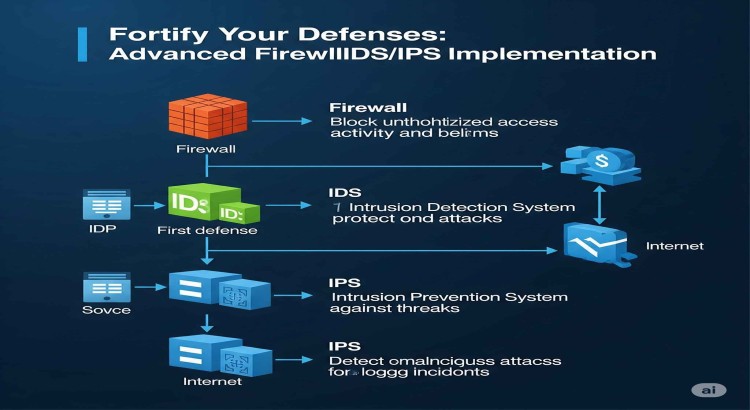
About this Service
Overview:
In an era of escalating cyber threats, robust network security is not an option, but a necessity. Data breaches, malware attacks, and unauthorized access can cripple operations, erode trust, and incur severe financial penalties. This offer is specifically designed for businesses committed to establishing an impenetrable digital perimeter through expert firewall administration and cutting-edge Intrusion Detection/Prevention Systems (IDS/IPS). With 8 years of specialized experience, I provide comprehensive security solutions that proactively identify, prevent, and mitigate cyber threats. I will configure and manage your firewalls, deploy advanced IDS/IPS, and establish robust security policies to safeguard your sensitive data, ensure compliance, and provide peace of mind, allowing you to focus on your core business without security concerns.
Tools & Skills:
- Firewall Platforms: FortiGate, Palo Alto Networks, Cisco ASA, pfSense, Sophos UTM, Check Point
- Intrusion Detection/Prevention Systems (IDS/IPS): Snort, Suricata, Cisco Firepower, FortiGuard IPS
- Security Protocols: IPsec VPN, SSL VPN, TLS, SSH
- Network Security Best Practices: Segmentation, Least Privilege, Zero Trust principles
- Vulnerability Management: Nessus, OpenVAS, Qualys
- Security Information and Event Management (SIEM): Splunk, ELK Stack (Elasticsearch, Logstash, Kibana) for log analysis
- Compliance Frameworks: GDPR, HIPAA, ISO 27001 (awareness and implementation support)
- Threat Intelligence Integration: Utilizing threat feeds for proactive defense.
- Incident Response Planning: Basic support in developing response procedures.
How I Work:
My approach to firewall administration and IDS/IPS implementation is multi-layered and security-first:
Security Assessment & Threat Analysis:
- Initial Consultation: Discussion to understand your current security posture, existing vulnerabilities, and compliance requirements.
- Network Security Audit: Comprehensive review of your current firewall rules, network segmentation, access controls, and existing security tools.
- Threat Landscape Analysis: Identification of potential threats relevant to your industry and infrastructure.
- Vulnerability Scan (Basic): Performing a basic external vulnerability scan to identify obvious weaknesses.
- Security Assessment Report: A detailed report outlining identified security gaps, potential risks, and recommended security enhancements.
Security Architecture Design & Planning:
- Customized Security Design: Development of a tailored security architecture, including firewall rule sets, network segmentation strategies, VPN configurations, and IDS/IPS deployment plans.
- Policy Definition: Creation of granular security policies to control traffic flow, prevent unauthorized access, and mitigate known threats.
- Implementation Blueprint: A detailed plan for deploying and configuring firewalls and IDS/IPS, including IP addressing, zone definitions, and rule prioritization.
- Client Review & Approval: Presentation of the proposed security plan for your review, feedback, and final approval.
Implementation & Configuration:
- Firewall Deployment/Configuration: Installation, configuration, and hardening of chosen firewall solutions (e.g., FortiGate, Palo Alto). This includes setting up NAT, routing, VPN tunnels, and security zones.
- IDS/IPS Integration: Deployment and configuration of Intrusion Detection/Prevention Systems (e.g., Snort, Suricata) to monitor network traffic for malicious activity and block threats in real-time.
- Rule Set Optimization: Creation and fine-tuning of firewall and IDS/IPS rule sets to maximize protection while minimizing false positives.
- Logging & Alerting Setup: Configuration of comprehensive logging and alerting mechanisms to ensure real-time visibility into security events.
- VPN Setup: Secure VPN (IPsec/SSL) configuration for remote access or site-to-site connectivity.
Testing, Validation & Hardening:
- Security Testing: Rigorous testing of firewall rules and IDS/IPS effectiveness, including simulated attacks and traffic analysis.
- Vulnerability Verification: Re-scanning to confirm that identified vulnerabilities have been addressed.
- Performance Impact Assessment: Ensuring that security measures do not unduly impact network performance.
- Security Hardening: Applying additional hardening techniques to network devices and servers to reduce attack surface.
Documentation & Ongoing Recommendations:
- Comprehensive Security Documentation: Provision of detailed documentation including firewall rule sets, IDS/IPS configurations, network segmentation maps, and security policies.
- Best Practices Guide: Recommendations for ongoing security posture management, regular updates, and continuous monitoring.
- Knowledge Transfer: A session to educate your team on managing and monitoring the new security infrastructure.
Why Choose Me?
- Deep Security Expertise: 8 years focused on network security, specializing in firewall and IDS/IPS technologies.
- Proactive Threat Mitigation: My solutions are designed to not only react to threats but to prevent them from reaching your network.
- Vendor Agnostic Proficiency: Experienced with leading firewall and IDS/IPS vendors, allowing for tailored solutions based on your existing infrastructure or specific needs.
- Layered Security Approach: Implementation of multi-layered defenses for comprehensive protection against evolving cyber threats.
- Focus on Business Continuity: Security measures are implemented with an understanding of operational impact, ensuring business continuity.
- Clear Communication & Reporting: You'll receive clear explanations of security risks and detailed reports on implemented solutions.
Service Features
- ● Initial security assessment and consultation
- ● Analysis of existing network security posture
- ● Configuration and hardening of one primary firewall device
- ● Implementation of essential firewall rules (up to 15 rules)
- ● Basic setup of an open-source IDS for monitoring
- ● Configuration of basic VPN (site-to-site or remote access for up to 5 users)
- ● Basic logging and alerting setup
- ● Summary report of implemented security measures
About the Seller
From
California, United States
Member Since
Oct 2024
Skills:
Reviews (1)

Samuel Gonzalez
Ciudad de México, Mexico
"Mr. Harrison delivered the project on time and was very professional."
Basic


Join as a freelancer or client
Join as a Freelancer
Join as a Client