Intrusion Detection Systems (IDS) Implementation & Management

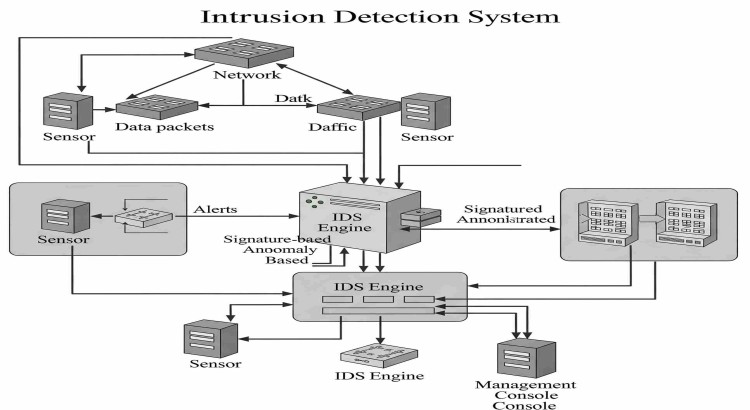
About this Service
My comprehensive services in this area include the following stages:
- Initial Security Assessment & Risk Analysis: Before any action, I conduct a thorough review of your current network architecture, existing security controls, and potential vulnerabilities. This assessment includes identifying critical network points and determining the optimal placement for IDS sensors to ensure maximum coverage and efficiency. The goal is to design optimal strategies for IDS placement and configuration.
- Custom IDS Solution Selection & Design: Based on your budget, network size, and specific security concerns, I guide you through the selection of appropriate IDS technologies (e.g., Snort, Suricata, Zeek/Bro). I design a scalable IDS architecture, whether host-based (HIDS), network-based (NIDS), or a hybrid approach, with the aim of comprehensive threat coverage.
- Precise Deployment & Configuration: Professional installation and meticulous configuration of IDS sensors and management consoles are performed. This process involves defining precise detection rules, signatures, and anomaly detection baselines to accurately identify known and unknown threats while minimizing false positives. I utilize advanced tools like Snort for custom rule definition and Suricata for deep packet analysis.
- Rule Customization & Optimization: I tailor IDS rulesets to your unique environment, business applications, and compliance requirements. Continuous optimization of rules to adapt to new threats and reduce "Alert Fatigue" is a top priority. This includes fine-tuning rule sensitivity and creating necessary exceptions.
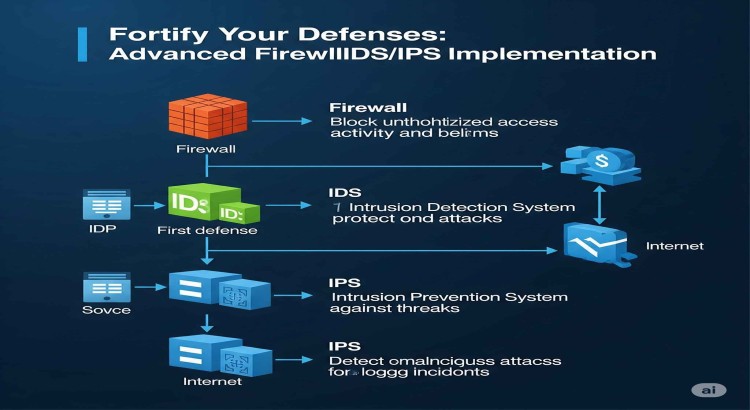
- Integration with Existing Security Tools: Seamless integration of the IDS with your Security Information and Event Management (SIEM) system, firewalls, and other security solutions for centralized logging, correlation, and automated incident response capabilities. This integration provides a more comprehensive view of the network's security posture.
- Alert Management & Incident Response Playbook Development: Establishing clear procedures for alert prioritization, analysis, and escalation. Assisting in the development of an "Incident Response Playbook" to ensure rapid and effective handling of detected security incidents. This includes defining step-by-step procedures for responding to various types of intrusions.
- Continuous Monitoring & Threat Analysis: Ongoing monitoring of IDS alerts and logs. Regular analysis of threat intelligence feeds to update IDS rules and actively identify emerging attack patterns relevant to your organization. This process involves periodic review of IDS reports and aligning them with the latest cyber threats.
- IDS Performance Optimization: Ensuring that the IDS operates efficiently without negatively impacting network performance, by optimizing resource consumption and data processing capabilities. This includes memory, CPU, and I/O settings for IDS sensors.
Why Choose Me?
With over 9 years of hands-on experience in managing and securing network infrastructures, I possess deep expertise in designing and implementing complex IDS solutions. My focus is on delivering high-availability and high-performance solutions that not only detect but also effectively help mitigate security risks. My proven track record includes significantly improving network performance and reducing network downtime by 25% for large-scale networks. I am committed to providing meticulous, detail-oriented service that ensures your network's security posture is robust and resilient against modern cyber threats.
Service Features
- ● Comprehensive IDS Setup & Configuration
- ● Custom Rule Development & Optimization
- ● Integration with SIEM/Firewall
- ● Initial Security Assessment & Reporting
- ● Alert Management & Basic Incident Response Guidance
About the Seller
From
California, United States
Member Since
Oct 2024
Skills:
Reviews (1)

Michael Tan
New South Wales, Australia
James completed the Intrusion Detection Systems (IDS) project for us. The quality of the work was fairly good, and the system appears to be working as intended. However, we found communication to be a bit challenging at times due to his busy schedule, and it was difficult to get timely updates on the project status. We had hoped for a bit more detail in the final delivery.
Basic




Join as a freelancer or client
Join as a Freelancer
Join as a Client