Expert Database Security Consulting

About this Service
As a dedicated Database Security Consultant with 8 years of specialized professional experience, I understand that your data is your most valuable asset. My unwavering commitment to detail ensures your databases are not just protected, but fortified against evolving threats. I offer comprehensive, precise, and fair-priced solutions to safeguard your critical information, ensuring confidentiality, integrity, and availability.
About My Database Security Consulting Service:
Overview:
As a specialized Database Security Consultant with 8 years of professional experience, I go beyond merely providing services; I become your trusted partner in safeguarding your critical data. My approach is founded on meticulous precision and unwavering commitment to making your databases impenetrable against ever-evolving threats. I provide comprehensive, accurate, and cost-effective solutions to ensure the confidentiality, integrity, and availability of your data.
What Services & How I Perform Them:
My process is structured and meticulous to ensure maximum security with minimal disruption. It involves:
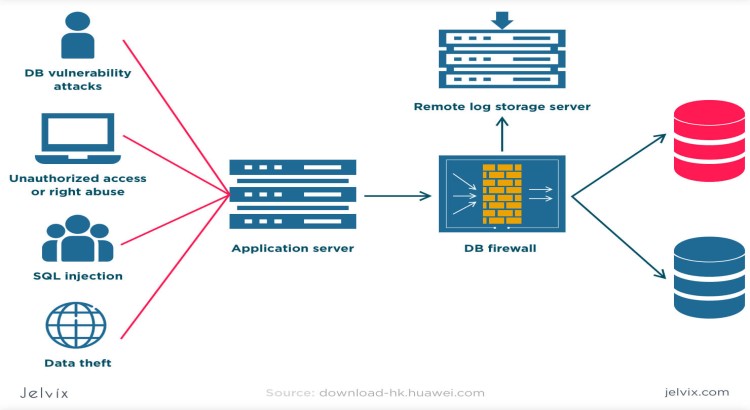
- Detailed Security Assessment & Vulnerability Analysis: I begin with a comprehensive review of your current database environment (including configurations, schema, and existing security controls) to pinpoint vulnerabilities, misconfigurations, and compliance gaps. This involves using a combination of manual checks, automated vulnerability scanners, and security best practice checklists specific to your database platform.
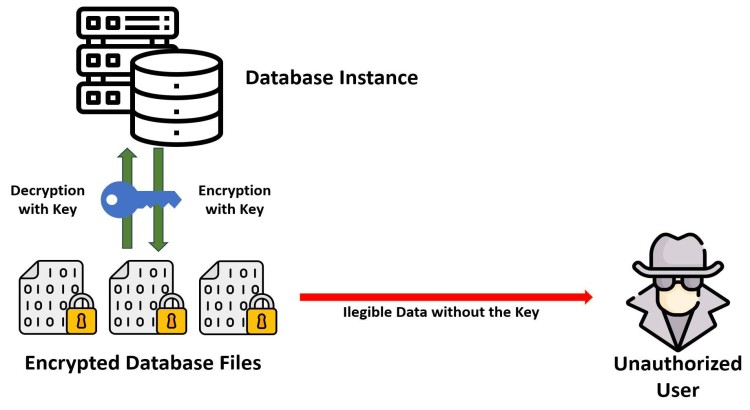
- Advanced Encryption Design & Implementation: I design and implement robust encryption strategies to protect your data at every stage. This includes Transparent Data Encryption (TDE) for data at rest, configuring SSL/TLS for secure data in transit, and implementing Column-Level Encryption or advanced features like Always Encrypted (for SQL Server) for highly sensitive data fields, ensuring data remains secure even if compromised.
- Granular Access Control & Least Privilege Enforcement: I establish stringent access controls based on the Principle of Least Privilege (PoLP), granting users and applications only the absolute minimum permissions required for their functions. This includes designing and implementing Role-Based Access Control (RBAC), hardening authentication mechanisms, and integrating with centralized identity management systems where applicable.
- Comprehensive Auditing, Logging & Compliance: I set up robust auditing mechanisms to record all security-relevant database activities, ensuring accountability. This involves configuring detailed audit trails, secure log management, and establishing retention policies to meet internal governance and external regulatory requirements (e.g., GDPR, HIPAA, PCI DSS, ISO 27001).
- Database Hardening & Best Practices Adherence: I apply industry-leading security hardening benchmarks and tailor them to your specific database platform. This includes disabling unnecessary services, closing unused ports, removing default accounts, and implementing secure configuration management to minimize the attack surface.
- Performance Impact Analysis & Optimization: Throughout the security implementation, I continuously monitor and analyze database performance. My goal is to ensure that all security enhancements are integrated seamlessly with minimal to no adverse impact on your database's speed and responsiveness.
Key Tools & Technologies I Utilize:
- Native Database Management Tools: SQL Server Management Studio (SSMS), Azure Data Studio, pgAdmin, Oracle SQL Developer.
- Security Assessment Tools: Specialized vulnerability scanners (e.g., SQLmap, Nessus, OpenVAS for network scans), database security assessment scripts.
- Encryption Technologies: TDE, Always Encrypted, SSL/TLS, database-specific encryption functions.
- Auditing & Logging Tools: SQL Server Audit, PostgreSQL Audit, Oracle Unified Audit, log management solutions (e.g., ELK Stack components, Splunk, Azure Monitor).
- Scripting & Automation: PowerShell, Python, Bash for automating security checks, reporting, and routine hardening tasks.
Scope of the Offer:
This offer covers the comprehensive security assessment, design, and implementation for one to two primary database instances/clusters (e.g., a production SQL Server instance, a PostgreSQL cluster, or a critical Oracle database). For larger environments, a custom quote will be provided. The focus is on on-premise, cloud-hosted (IaaS VMs), or PaaS database services where direct configuration access is available.
My Areas of Mastery:
- Database Platforms
- Security Frameworks
- Encryption Technologies
- Access Control
- Auditing & Monitoring
- Vulnerability Management
- Cloud Database Security
Why Partner With Me?
- 8 Years of Dedicated Expertise: My professional journey has been focused entirely on database administration and security, equipping me with deep insights and practical, hands-on experience across various enterprise environments.
- Meticulous Attention to Detail: As a specialist, I pride myself on my precision. Every configuration and recommendation is thoroughly vetted to ensure no vulnerability is overlooked.
- Committed Partnership: I approach every project with a strong sense of ownership and dedication, working as a true partner to achieve your security goals. Your data's safety is my priority.
- Fair & Transparent Pricing: My rates reflect the high value and expert-level service you receive, with transparent proposals and no hidden costs.
Service Features
- ● Database Security Audit & Assessment
- ● Advanced Encryption Implementation
- ● Granular Access Control & PoLP Enforcement
- ● Comprehensive Auditing, Logging & Compliance
- ● Database Hardening & Best Practices
- ● Performance Impact Analysis
- ● Documentation & Knowledge Transfer
- ● Post-Implementation Advisory Support
About the Seller
From
North Denmark Region, Denmark
Member Since
May 2025
Skills:
Basic


Join as a freelancer or client
Join as a Freelancer
Join as a Client